Phishing attacks are online scams in which hackers pretend to represent reliable organizations to trick victims into disclosing private information like passwords or credit card numbers.
Attackers frequently use phony emails, texts, and websites to dupe victims into acting—such as clicking on a dangerous link or giving out personal information—by appearing to be a trustworthy source.
These assaults prey on human weaknesses and can cause identity theft, financial fraud, or unauthorized account access.
You can safeguard yourself by being wary of unsolicited messages, checking the source, looking out for telltale indicators of deception, using legitimate channels, maintaining software updates, and becoming knowledgeable about phishing tactics.
Possible Phishing Attack Types Used by Hackers
- Bait: The attacker typically imitates well-known companies or services to create a message or webpage that appears natural. They could utilize official email accounts, web page layouts, or logos to appear legitimate.
- Hook: A request to take action, such as clicking on a link, opening an attachment, or inputting personal information, is made in the message or website. To improve the possibility that the victim will cooperate, the assailant may employ various techniques to instill a sense of urgency or fear.
- Catch: If the victim acts as expected, they might unintentionally divulge private information or provide access to their system. For instance, the attacker could obtain their username and password by entering their login information on a bogus website.
- Exploit: With the information in hand; the attacker can utilize it for various nefarious activities, including gaining unauthorized access to accounts, identity theft, financial fraud, or even initiating follow-up assaults on other people or entities.
Types of Phishing Attacks

- Email Phishing: This kind of phishing attack is the most common. Attackers send misleading emails that seem to be sent by reputable organizations like banks, social networking sites, or governmental bodies. The intensity of the emails frequently tempts recipients to click on harmful links, download malicious attachments, or expose personal information.
- Spear Phishing: Attacks using spear phishing are more specific and targeted. Attackers research their targets and create customized messages to encourage them to act. They can leverage data gathered from social media or other sources to make the emails seem more convincing and raise their odds of success.
- Whaling: Attacks on whales are directed explicitly against high-profile people, such as CEOs, top executives, or public figures. Attackers pose as reliable people or businesses to trick their targets into divulging confidential information or carrying out financial transactions.
- Smishing: Sending victims false text messages is a simple SMS phishing method. These messages frequently have an urgency or a tempting offer, which prompts recipients to click on harmful links or text back personal information.
- Vishing: Vishing, often known as voice phishing, is when attackers use phone calls to persuade someone to disclose important information. To trick victims into revealing personal information or financial details over the phone, they may act as bank employees, tech support specialists, or government agents and use social engineering techniques.
- Pharming: Even when a victim types the right URL into their browser, pharming attacks modify the Domain Name System (DNS) to reroute them to malicious websites. Attackers can gather their login information or other sensitive data by tricking visitors into thinking they are accessing reputable websites.
- Clone Phishing: Clone phishing entails making an almost exact clone of an authentic email or website. Attackers copy real emails or websites, make minor changes, and then transmit the copies to their targets. To get accurate, recipients can fail to recognize the discrepancies and provide the attackers with sensitive information.
- Man-in-the-Middle (MitM) Attacks: Attackers discreetly pass information back and forth between two parties while intercepting and changing conversations in a MitM attack. Attackers can eavesdrop on private information, such as login passwords or financial information, by acting as the “middle” entity.
Methods to Identify Phishing Attacks
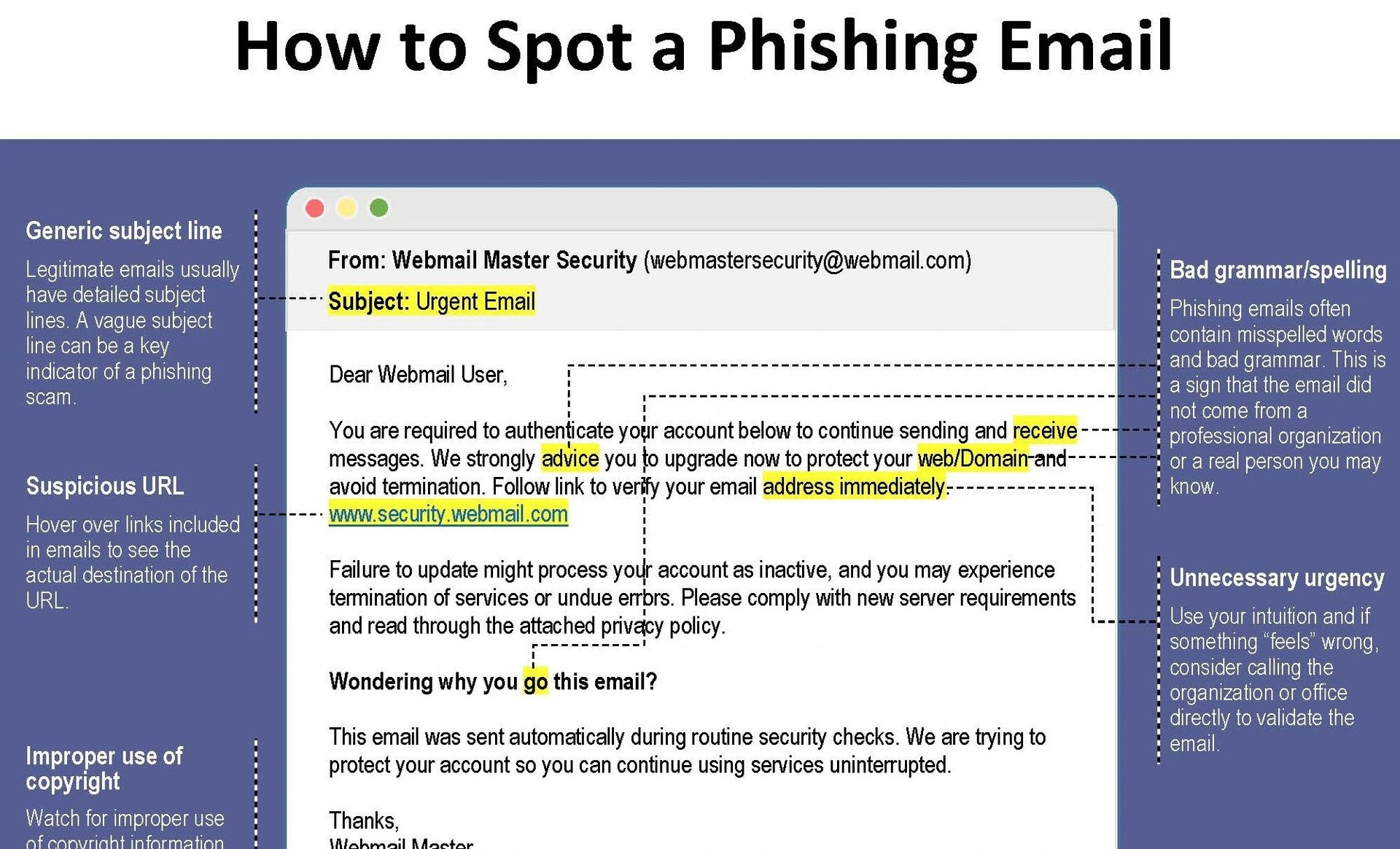
- Check the sender’s email address: Pay close attention to the sender’s email address. Authentic domain names are frequently slightly altered or misspelled in phishing emails. Instead of “https://paypal.xn--com%2C-1i0c/ for instance, use “paypalsecurity.com.” If the email domain seems suspicious or unfamiliar, use caution.
- Look for generic greetings: Phishing emails frequently refer to you by name instead of generic greetings like “Dear Customer” or “Dear User.” Genuine businesses typically use your name to personalize their communications.
- Watch for spelling and grammar mistakes: Grammar and spelling mistakes are frequent in phishing emails. An email filled with errors is a warning sign because professional organizations typically have stringent quality control.
- Check for urgent or threatening language: Phishing emails frequently generate a sense of urgency or anxiety to get you to respond right away. They can threaten to close your account, accuse fraud, or issue a grave warning if you don’t answer right away. Be aware of such strategies.
- Hover over links: To view a link URL without clicking, move your mouse cursor over it in an email. The link content in phishing emails might not match the desired target. Make that the URL points to the organization’s legitimate website.
- Beware of requests for personal information: You will never be requested to email personal information to reputable companies. Be wary whenever you receive an email requesting private information like passwords, Social Security numbers, or credit card numbers. Reputable companies typically securely handle such information.
- Examine email formatting and logos: Pay attention to how the email looks. A phishing effort can be identified by emails with poor formatting, mismatched typefaces, distorted logos, or low-quality graphics.
- Be cautious of unexpected attachments: Phishing emails could include attachments with viruses or malware. Do not open any unexpected attachments you receive from unidentified or suspicious sources.
- Verify through official channels: Check the credibility of every email you get that purports to be from a particular company. Contact the company using their official website or phone number to verify the communication is honest.
- Trust your instincts: It is best to take the route of caution if something seems wrong or too fantastic to be true. It is preferable to delete an email or report it to the proper authority if you have any suspicions about its legality.
Phishing Attacks Prevention Checklist
- Identify Phishing
- False sense of security
- Do not click on unknown links
- Never trust unknown sites
- Hardly ever disclose personal information
- Upgrade your software
- Block Pop – Ups
- Enable Firewalls
- Enable 2 FA or Passwordless Authentications
- Raise Phishing Awareness

Identify Phishing
- Generic greeting: Instead of addressing you by name at the beginning of the email, it begins with the generic greeting “Dear Client.” Authentic businesses typically customize their communications.
- Urgent language: The email conveys a sense of urgency by stating that there are security issues and that immediate action is necessary. Phishing efforts frequently employ urgency or panic to get you to respond without thinking.
- Suspicious link: The email includes a link that says, “Click here to validate your account right away.” You should exercise caution while clicking on these links, though. To see the link’s actual URL before clicking, move your mouse cursor over it. In this instance, the link can take you to a bogus website made to steal your login information.
- Lack of personalization: Your name or login will usually be used in correspondence with trustworthy companies. This email’s lack of personalized information raises suspicions that it is not authentic.
- Poor grammar or spelling errors: Phishing emails often contain spelling or grammatical mistakes. This example has no specific errors, but it’s always a good idea to be cautious of such errors in email communications.
- Unusual sender’s email address: Scrutinize the sender’s email address. Email addresses that appear professional but may be slightly different or misspelled are frequently used in phishing emails. In this situation, verifying the integrity of the sender’s email address is essential.
2. False sense of security
- Trust in security measures: Individuals may only use security technologies like firewalls, antivirus programs, or spam filters to keep them safe from phishing attempts. These technologies are crucial but imperfect and might not detect all phishing attempts. A false sense of security may result from relying only on technology.
- Lack of awareness: Some people might not know how common and sophisticated phishing assaults are. They could disregard the dangers and believe they are improbable targets. They might be less watchful and more likely to be duped by phishing schemes due to their ignorance.
- Previous success in avoiding phishing attempts: Someone may create the misconception that they are resistant to phishing attacks if they have never been the target of one or have successfully recognized and avoided them. This overconfidence may cause complacency and a loss of alertness while dealing with suspicious emails or communications.
- Familiarity with the sender or context: By receiving emails or messages in familiar settings or from sources they trust, people are more inclined to down their guard. Attackers take advantage of this by pretending to be reputable organizations like banks, social media sites, or coworkers in order to earn the trust of their victims and coerce them into disclosing personal information.
- Social engineering techniques: Psychological manipulation techniques are frequently used by phishing attackers to target human weaknesses and get around security barriers. To get victims to act immediately without questioning the communication’s validity, they create feelings of urgency, panic, or interest.
3. Do not click on unknown links
Here’s why you should be cautious about clicking on unknown links in phishing attacks:
- Malware distribution: A malicious link can cause your device to download malware if you click on it. This malware may contain viruses, spyware, ransomware, or other harmful applications that might damage your computer or compromise security by stealing sensitive data.
- Credential theft: Phishing links can take you to fake websites that seem like genuine ones. These websites are made to mislead you into providing your username and password for login. By doing this, you unintentionally give hackers access to your sensitive data and grant them unrestricted access to your accounts.
- Fake websites and forms: Phishing links may take you to fake websites that look like well-known businesses, like banks, e-commerce sites, or social networking networks. These websites frequently use appealing login pages or forms to collect your financial and personal information. You put yourself at risk of identity theft or financial crime by clicking on such links and providing your information.
- Drive-by downloads: Some phishing links might download automatically without your permission. These downloads could contain harmful software that compromises your data, damages your system, or grants hackers unrestricted access to your device.
4. Never trust unknown sites
- Identity theft: Phishing websites deceive visitors into revealing sensitive information, including usernames, passwords, credit card numbers, and social security numbers. If you enter this information on an untrusted website, attackers may get a hold of it and use it for fraud, identity theft, or other malicious purposes.
- Financial fraud: Phishing sites may ask for banking or payment information to deceive visitors into carrying out fraudulent activities. Giving such sensitive information to an untrusted website puts you at risk of financial loss or unauthorized access to your accounts.
- Malware distribution: Browsing unidentified websites puts your device at risk of malware attacks. Phishing websites may try to secretly and automatically download harmful malware to your computer or mobile device. As a result, your system may experience security breaches, data loss, or unwanted access.
- Phishing page redirection: Phishing links might send you to unidentified websites that act as traps to gather your personal data. Even if you first land on what appears to be a dedicated page, further links or actions on the website could direct you there. Trusting such websites could have adverse effects.
5. Hardly ever disclose personal information
- Identity theft: Identity theft may occur if you provide phishing attackers with your personal information. They could use the data you give them to pose as you, get access to your accounts without authorization, apply for credit in your name, or carry out other illegal acts.
- Financial fraud: Your personal information may be used by phishing attackers to commit financial fraud. They may use your credit card number or bank account information to carry out unauthorized transactions, which could result in financial loss and harm to your credit report.
- Account compromise: Sharing login credentials or account information with phishing attackers can compromise your accounts. They can log in to your funds, access sensitive data, conduct unauthorized activities, or take control of your online presence.
- Targeted phishing attacks: Your accounts could be compromised if you provide phishing attackers with your login information or other account details. They can access your accounts, gain access to private information, engage in unauthorized behavior, or take control of your online identity.
6. Upgrade your software
- Patching security vulnerabilities: Patches and fixes for known vulnerabilities are frequently incorporated into software updates. By making sure that any holes are fixed, you may lower the chance that attackers would use your software for phishing or other harmful purposes by making sure your software is up to date.
- Improved security features: These updates could include additional anti-phishing safeguards, more robust authentication procedures, or better data encryption, making it more challenging for attackers to trick or infiltrate your system.
- Protection against new phishing techniques: Attackers use new strategies to get around security precautions and deceive victims in phishing assaults. Updated algorithms and detection techniques mainly developed to block new phishing techniques may be included in software upgrades, protecting you better against the most recent threats.
- Browser security enhancements: Phishing scams frequently target web browsers. Updates to browsers frequently incorporate security improvements to block well-known phishing websites, alert you to suspicious links, or enhance your browsing experience’s overall security.
7. Block Pop – Ups
- Prevention of deceptive pop-up messages: Pop-up windows may include false messages showing clear alerts from reputable sources. It can be stated in these notifications that your account has been compromised, that you have won a prize, or that you need to take immediate action.
- Avoidance of fake login screens: To obtain your login information, phishing pop-ups may imitate popular websites’ or services’ login windows. By preventing the appearance of these false login pages, pop-up blocking lowers the possibility that you will mistakenly reveal your username and password to attackers.
- Protection against malicious content: Some phishing pop-ups have dangerous software or scripts that might harm your device. The chance of accidentally running these malicious scripts or downloading harmful files is reduced by blocking pop-ups.
8. Enable Firewalls
- Network traffic filtering: Firewalls examine traffic and prevent illegal or suspicious connections. They can identify and stop phishing efforts by preventing access to well-known phishing websites or by seeing fraudulent behavior in network packets.
- Protection against malicious downloads: Malicious files or viruses are frequently downloaded onto your device as part of phishing attacks. By preventing potentially hazardous downloads from accessing your system and increasing the risk of infection, firewalls can examine and prevent them.
- Defense against remote access attempts: Phishing attackers could attempt to gain unauthorized access to your device or network using remote control software or backdoors. Firewalls can watch incoming connections, and suspicious attempts can be stopped, restricting illegal access and any data breaches.
- Filtering of malicious email attachments: Incoming email attachments can be checked by firewalls for known malicious information. This assists in detecting and stopping phishing emails that may include dangerous attachments that trigger security vulnerabilities or run malicious code.
9. Enable 2 FA or Passwordless Authentications
- Protection against stolen credentials: Users are frequently fooled into revealing their usernames and passwords in phishing attacks. By activating 2FA or passwordless authentication, you can prevent attackers from accessing your account even if they manage to get your login information through phishing by requiring them to provide an additional factor, such as a verification code or biometric authentication.
- Mitigation of credential reuse: Many people use the same passwords for numerous accounts, which increases the danger of having one account compromised. Even if a hacker manages to get their hands on your password through phishing, they won’t be able to access your account without the secondary authentication factor with 2FA or passwordless authentication.
- Resistance to phishing attacks: Making fraudulent login pages or forms is a common tactic used in phishing attacks to obtain user information. With 2FA or passwordless authentication, even if you unintentionally provide a phishing website your login credentials, the attackers will be unable to get around the extra authentication step needed to access your account.
- Increased security through additional factors: 2FA often includes a second factor, such as a physical security key, a biometric scan (such as a fingerprint or facial recognition), or a verification code sent to your mobile device. Attackers would need both your login details and real ownership of the second factor, making it far more difficult for them to pass as you due to these additional factors.
10. Raise Phishing Awareness
- Education and training programs: Provide thorough training programs that inform people about phishing attempts, their variations, and the methods used by attackers. These courses should to cover subjects including identifying suspicious emails, detecting phishing Websites, understanding social engineering techniques, and promoting safe online conduct.
- Phishing simulations: Hold regular phishing simulations within businesses or educational institutions to provide employees and students with practical experience in spotting and responding to phishing attacks. In these simulations, fake phishing emails are sent to employees or students to assess their responses and give them rapid feedback.
- Awareness campaigns: Conduct recognition activities to draw attention to the risks posed by phishing scams and the necessity of being alert. To reach a large audience and reinforce important messages, use various communication channels, including newsletters, posters, email bulletins, social media, and internal messaging systems.
- Provide real-life examples: Provide real examples of phishing emails or websites to show how attackers disguise their intentions and mislead hacker victims. Examine these instances to identify the common patterns and strategies, such as urgency, scare tactics, spoof email addresses, and misleading URLs.
- Teach email hygiene: Focus on simple email hygiene, like avoiding suspicious links and downloading files from unreliable sources. Instruct people to double-check the legitimacy of emails, watch out for phishing warning signals (such as poor syntax, unexpected requests, or strange URLs), and report any suspicious emails to the relevant IT or security staff.
- Regular updates and reminders: Remind people regularly of the value of being aware of phishing by providing them updates and reminders. To keep people alert, distribute information about new phishing strategies, previous attacks, or notable trends.
- Stay updated with security measures: Inform them of the most recent security measures, such as password managers, two-factor authentication (2FA), and safe browsing techniques. In establishing another line of defense against phishing attacks, promote the use of these measures.
Article from Cyber Security News